Quantifying Energy Overhead in SCADA Cybersecurity Using AI-Based Threat Detection Models
DOI:
https://doi.org/10.71346/utj.v1i2.19Keywords:
AI-driven cybersecurity, SCADA systems, Energy-efficient intrusion detection, Deep learning anomaly detection, Generative adversarial networks, Adaptive security frameworks, Model optimization techniques, Power-aware machine learning, Industrial control system security, Energy consumption analysisAbstract
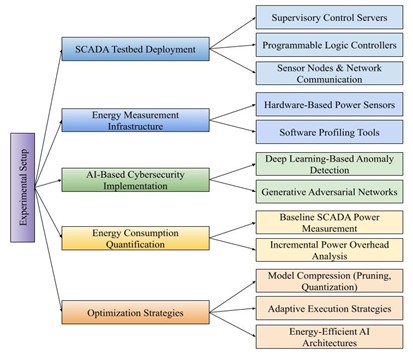
The increasing reliance on AI-driven cybersecurity solutions in SCADA environments has introduced significant computational demands, raising concerns about energy consumption in critical industrial systems. This research addresses the gap in existing studies which focus on security effectiveness while overlooking the energy implications of deploying deep learning-based intrusion detection mechanisms. The study presents an empirical analysis quantifying the energy footprint of AI-based cybersecurity approaches including convolutional recurrent networks, generative adversarial networks, and adaptive hybrid models within a realistic SCADA testbed. Energy profiling is conducted using high-resolution hardware instrumentation and software-based power monitoring techniques capturing variations in power usage across different AI models and deployment strategies. The findings demonstrate that while advanced AI models enhance security detection capabilities, they incur substantial energy costs which can be mitigated through model optimization techniques such as pruning quantization and knowledge distillation. Adaptive execution strategies further reduce power consumption by dynamically modulating AI processing complexity based on real-time threat assessments. The study establishes a foundation for developing energy-efficient cybersecurity frameworks that balance security resilience with operational sustainability. These insights inform industry best practices and contribute to future research on low-power AI models, decentralized security architectures, and energy-conscious industrial cybersecurity solutions ensuring effective protection of critical infrastructure without excessive resource burdens.
References
Alzahrani and T. H. H. Aldhyani, “Design of efficient based artificial intelligence approaches for sustainable of cyber security in smart industrial control system,” Sustainability, vol. 15, no. 10, p. 8076, May 2023, doi: 10.3390/su15108076.
Y. Luo, Y. Xiao, L. Cheng, G. Peng, and D. Yao, “Deep learning-based anomaly detection in cyber-physical systems,” ACM Computing Surveys, vol. 54, no. 5, pp. 1–36, May 2021, doi: 10.1145/3453155.
S. Brudni, S. Anidgar, O. Brodt, D. Mimran, A. Shabtai, and Y. Elovici, Green Security: A Framework for Measurement and Optimization of Energy Consumption of Cybersecurity Solutions. IEEE, 2024, pp. 676–696, doi: 10.1109/eurosp60621.2024.00043.
V. Varadharajan, U. Tupakula, and K. K. Karmakar, “Techniques for enhancing security in industrial control systems,” ACM Transactions on Cyber-Physical Systems, vol. 8, no. 1, pp. 1–36, Oct. 2023, doi: 10.1145/3630103.
K. Al-Dosari, N. Fetais, and M. Kucukvar, “A shift to green cybersecurity sustainability development: Using triple bottom-line sustainability assessment in Qatar transportation sector,” Int. J. Sustainable Transportation, vol. 17, no. 12, pp. 1287–1301, Feb. 2023, doi: 10.1080/15568318.2023.2171321.
H. Sarker, “Machine learning for intelligent data analysis and automation in cybersecurity: Current and future prospects,” Annals of Data Science, vol. 10, no. 6, pp. 1473–1498, Sep. 2022, doi: 10.1007/s40745-022-00444-2.
N S. Muthubalaji et al., “An intelligent big data security framework based on AEFS-KENN algorithms for the detection of cyber-attacks from smart grid systems,” Big Data Mining and Analytics, vol. 7, no. 2, pp. 399–418, Apr. 2024, doi: 10.26599/bdma.2023.9020022.
J. Park, J. Lee, Y. Kim, J.-G. Park, H. Kim, and D. Hong, “An enhanced AI-based network intrusion detection system using generative adversarial networks,” IEEE Internet of Things Journal, vol. 10, no. 3, pp. 2330–2345, Oct. 2022, doi: 10.1109/jiot.2022.3211346.
R. Santhi and P. Muthuswamy, “Industry 5.0 or Industry 4.0S? Introduction to Industry 4.0 and a peek into the prospective Industry 5.0 technologies,” Int. J. Interactive Design and Manufacturing (IJIDeM), vol. 17, no. 2, pp. 947–979, Feb. 2023, doi: 10.1007/s12008-023-01217-8.
S. Roy, S. Sankaran, and M. Zeng, “Green intrusion detection systems: A comprehensive review and directions,” Sensors, vol. 24, no. 17, p. 5516, Aug. 2024, doi: 10.3390/s24175516.
M. Y. Koay, R. K. L. Ko, H. Hettema, and K. Radke, “Machine learning in industrial control system (ICS) security: Current landscape, opportunities and challenges,” J. Intelligent Information Systems, vol. 60, no. 2, pp. 377–405, Oct. 2022, doi: 10.1007/s10844-022-00753-1.
Z. deWardener, “Defining the digital twin for Industry 4.0,” 2023, doi: 10.23860/thesis-2438.
H. Sedjelmaci, S. M. Senouci, and T. Taleb, “An accurate security game for low-resource IoT devices,” IEEE Transactions on Vehicular Technology, vol. 66, no. 10, pp. 9381–9393, May 2017, doi: 10.1109/tvt.2017.2701551.
J. Arshad, M. A. Azad, M. M. Abdellatif, M. H. U. Rehman, and K. Salah, “COLIDE: A collaborative intrusion detection framework for Internet of Things,” IET Networks, vol. 8, no. 1, pp. 3–14, Sep. 2018, doi: 10.1049/iet-net.2018.5036.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Tesfa Tegegne , Abeer Naser Faisal

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Authors retain copyright for all articles published in CrossLink Studies journals. These articles are made freely available under a Creative Commons CC BY-SA 4.0, which allows unrestricted downloading and reading by the public.




